Title: Unraveling the Web of Dependency Confusion: Strategies for Mitigation
In the intricate tapestry of modern software development, dependency management is a critical component. However, this interconnectedness also introduces a potent vector for cyberattacks, notably through a method known as dependency confusion. This attack exploits the way software packages manage dependencies, potentially allowing attackers to inject malicious code into an organization’s proprietary software. This blog post aims to dissect the mechanics of dependency confusion attacks, underscore their implications, and lay out a comprehensive blueprint for mitigation, advocating for a proactive stance in securing software supply chains.
Peeling Back the Layers: Understanding Dependency Confusion
My Perspective: Knowledge is Our Strongest Weapon
Dependency confusion attacks hinge on the manipulation of a package manager’s resolution process. Developers often use open-source libraries or packages as dependencies in their projects, which are managed through package managers. These dependencies are fetched from public repositories unless specified otherwise. Attackers exploit this by publishing malicious packages to these public repositories, naming them after internal packages used by target organizations. When the package manager attempts to resolve the dependency, it may mistakenly download the malicious package instead of the internal one, due to name confusion. This attack not only demonstrates the ingenuity of cyber adversaries but also highlights the vulnerabilities inherent in dependency management practices.
The Fallout: Implications of Dependency Confusion Attacks
My Perspective: The Stakes Are Higher Than Ever
The ramifications of a successful dependency confusion attack are far-reaching. They can lead to the compromise of sensitive information, unauthorized access to internal systems, and the potential introduction of malware into an organization’s software ecosystem. The subtlety of this attack vector is particularly alarming; it can bypass many traditional security measures, embedding itself within the normal workflow of software development. As organizations increasingly rely on open-source components and external libraries, the risk of such attacks becomes more pronounced, underscoring the need for enhanced vigilance and security measures.
A Closer Look: The “SecureCorp” Scenario
Imagine a hypothetical company, SecureCorp, that relies on a proprietary library named secure-utils for its projects. This library is integral to SecureCorp’s operations and is hosted on their private package repository. However, due to the nature of dependency resolution processes, an attacker manages to exploit this setup by creating a malicious package with the same name and publishing it to a public repository. This leads to SecureCorp inadvertently integrating the malicious package into their systems, demonstrating the stealth and efficiency of dependency confusion attacks.
The Attack Illustrated
To better understand the process, consider the following illustration which visualizes the dependency confusion attack:
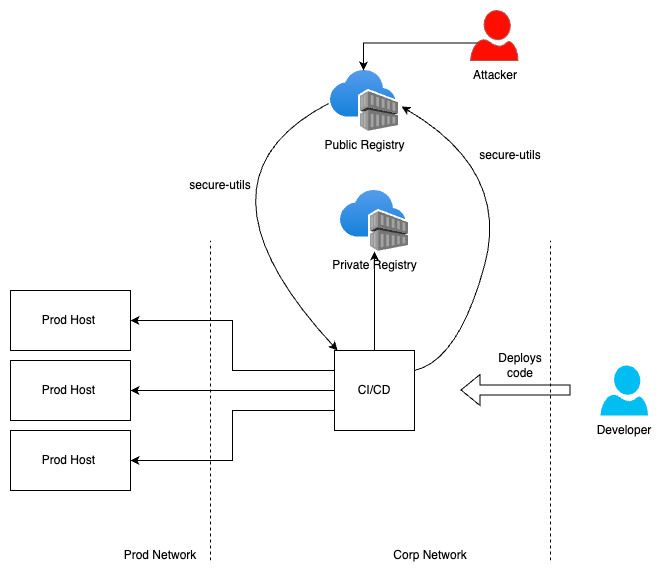
The diagram showcases two paths for dependency resolution: the correct path leading to SecureCorp’s internal package and the malicious path leading to the public repository. This visual representation underscores the critical error point where the package manager is deceived into fetching the wrong package due to the dependency confusion tactic.
Charting a Course: Strategies for Mitigation
My Perspective: A Multifaceted Defense is Paramount
Mitigating the risk of dependency confusion requires a holistic approach, combining technical safeguards with organizational policies. Essential strategies include establishing a private package registry, scoping packages, implementing a rigorous dependency review and approval process, and integrating automated vulnerability scanning. Additionally, education and awareness among developers about the risks associated with dependency confusion are crucial for fostering a culture of security.
Conclusion: Securing the Links in Our Chain
The threat posed by dependency confusion attacks to the software supply chain underscores the need for vigilant, proactive security measures. By understanding the mechanics of these attacks and adopting a comprehensive mitigation strategy, organizations can protect their digital infrastructure from being compromised. As we navigate the complexities of software development in an increasingly interconnected world, let us commit to a future where security is not just a response but a foundational aspect of our technological endeavors.