Background
This particular bug was a application specific bug that allowed an attacker to make user share a post on social media with some user interaction. This isin’t much fancy but this was the bug that helped me get over a burnout.
Attack Vector
The website allowed users to write articles and share them publically. Since, this was a private program, I cannot disclose their name but I hope you are able to understand their functionality based on my description. The website had embedded social media buttons that allow users to share the current websites link.

Upon inspecting the element, I found that there was falling javascript event that was run in the onclick() method.
function() {
var e = encodeURIComponent("Check out this post on REDACTED"),
t = "https://twitter.com/intent/tweet?url=" + window.location.href + "&text=" + e;
window.open(t, "ShareOnTwitter", yp()).opener = null
}
This means that the URL from the user is accepted using window.location.href and then appended to the twitter’s url parameter. Moreover, the text parameter is assigned a static value e which is set to "Check out this post on REDACTED". After assigning both these values a window is opened that looks as follows:
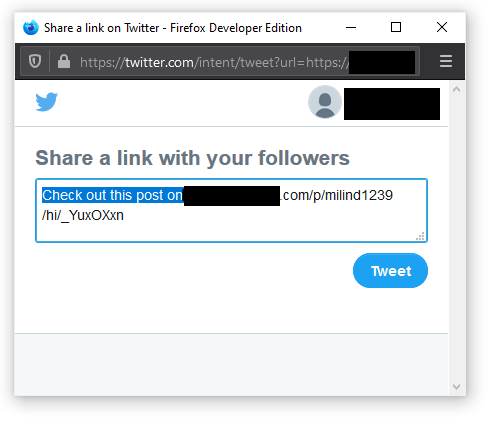
Since, the value is accepted from the window.location.href all I need to do is take control of that. I tried to tamper with the parameter and injected my own text parameter there by manipulating the URL as follows:
https://REDACTED/p/milind1239/hi/_YuxOXxn?text=pandaonair
and I got the following response in the tweet box:
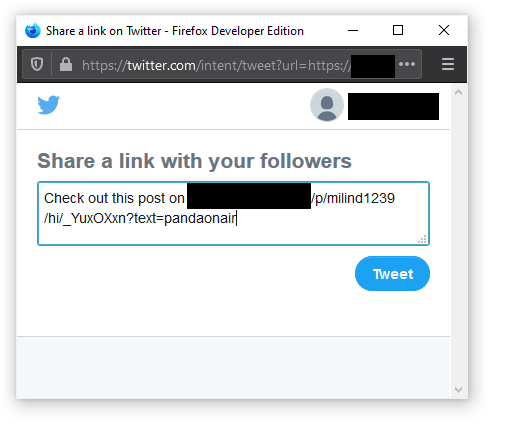
This confirmed that I could inject values in the tweet box, however, this still wasnt’t enough to take control of the tweet box. Then I tampered with the box even more and finally deviced the perfect payload that allowed me take control of the tweet box’s content completely.
https://REDACTED/p/milind1239/hi/_YuxOXxn?u=1%20&text=pandaonair

Here %20 is nothing but a space parameter. The twitter url requires 2 parameters url and text. When you insert a space in the url, the url parameter is ignored by twitter and only the 1st text parameter is rendered. If you want, you can confirm this by going to 2 of these urls:
https://twitter.com/intent/tweet?url=https://pandaonair.com/?u=1&text=pandaonair
and now add a space between u=1 and &text=pandaonair.com; something like this:
https://twitter.com/intent/tweet?url=https://pandaonair.com/?u=1 &text=pandaonair
Now I can inject anything in the text parameter. Ofcourse, I cannot just enter any URL because users aren’t so stupid. All I did was entered URL of another post (Something like this:)
https://REDACTED/p/hkrlol/Hahaha/LMAmBre0?u=1 &text=Check%20out%20this%20post%20at%20REDACTED%20https://REDACTED/p/milind1239/This-is-not-the-original-article/wKXbn5mZ
This kind of broke the functionality of the feature. Since the users aren’t gonna notice the change in URL address anyway the attack would go much more smoothly. The victim would read another URL here but his shared URL would be different. Ofcourse there is some user interaction that is required in this case but this wasn’t one of thoes cases where user interaction is unlikely. This interaction process is part of the normal flow that a user would do inorder to share a post.
Conclusion:
For Hackers: Whenever you see a target that has embeded share buttons, try to inject a parameter in the end to the URL and then see if the tweet button reflects the parameter in the content. If it does, it might be your lucky day.
For Developers: Never accept urls using window.location.href or on the client side; if you do so, make sure that the parameters are well sanatized. If possible always store thoes values into the parameters on the server side.
Timeline:
March 2. 2020: Reported to Program
March 3, 2020: Closed as Informative
March 5, 2020: Acknowledged and Triaged
March 6, 2020: Bounty Awarded
March 20, 2020: Fixed
I hope you guys had fun reading this blog post. Do let me know in the comments how you felt or if you have any doubts, DM me on twitter @panda0nair
Thanks,